Figure 18-1 Security Restrictions for remote operations.
| Previous | Table of Contents | Next |
Use the setfacl -d command to delete an ACL entry. To delete the entry, you can specify the entry type and the UID or GID. You do not need to include the permissions as part of the argument to the -d option.
Type the following syntax to delete an ACL entry and then press Return:
setfacl -d<entry_type>:<UID> | <GID> <filename1> [<filename2>] [<filename3>]
In the following example, user ray is deleted from the ACL of the file foo.
castle% setfacl -d u:ray foo castle% getfacl usage: getfacl [-ad] file ... castle% getfacl foo # file: foo # owner: winsor # group: staff user::rw- group::rw- #effective:rw- mask:rw- other:rw- castle%
You can copy ACL file permissions from one file to another without specifying them on the command line by piping the output of getfacl <filename> to another file by typing the following syntax and pressing Return:
getfacl <filename1> | setfacl -f - <filename2>
In the following example, the ACL for file foo is used as the template for the ACL for file bar.
First, verify that the files have different ACL permissions:
castle% getfacl foo bar # file: foo # owner: winsor # group: staff user::rw- user:ray:rwx #effective:rw- group::rw- #effective:rw- mask:rw- other:rw- # file: bar # owner: winsor # group: staff user::rw- group::rw- #effective:rw- mask:rw- other:rw-
Then list the ACL using the getfacl command and pipe the output to the setfacl -f command. The dash (-) tells the setfacl command to use the output from the file specified for the getfacl command as input to the second file.
castle% getfacl foo | setfacl -f - bar
Finally, use the getfacl command to verify that both files now have the same ACL permissions:
castle% getfacl foo bar # file: foo # owner: winsor # group: staff user::rw- user:ray:rwx #effective:rw- group::rw- #effective:rw- mask:rw- other:rw- # file: bar # owner: winsor # group: staff user::rw- user:ray:rwx #effective:rw- group::rw- #effective:rw- mask:rw- other:rw- castle%
Networks create an interesting access and security paradox. Users on a network almost always push for freer access to information and files. System administrators almost always push for more restrictive access to information and files so that they can more effectively monitor use and secure access to sensitive information.
Network security is usually based on limiting or blocking operations from remote systems.
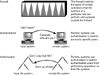
Network security comprises three aspects: firewall, authentication, and authorization, as illustrated in Figure 18-1.

Figure 18-1 Security Restrictions for remote operations.
The purpose of creating a firewall network security system is to ensure that all of the communication between a local network and an external network conforms to your local network security policy. A network security policy can be permissive or restrictive. A permissive policy might allow access to all services unless specifically denied. A restrictive policy might deny access to all services unless specifically allowed.
You can set up a firewall system to help protect the resources in your network from outside access. A firewall system acts as a barrier between your internal network and outside networks.
The firewall has two functions:
CAUTION! A firewall prevents unauthorized users from accessing hosts on your network. Maintain strict and rigidly enforced security on the firewall. However, an intruder who can break into your firewall system may be able to gain access to all of the other hosts on the internal network.
A firewall system should not have any trusted hosts. A trusted host is one from which a user can log in without being required to type in a password. The firewall system should not share any of its file systems or mount any file systems from other servers.
You can use ASET to make a system into a firewall and to enforce high security on a firewall system. For more information on ASET, refer to Chapter 20.
Two good reference books on firewalls are Firewalls & Internet Security: Repelling the Wily Hacker by Steven Cheswick and William Bellovin and Building Internet Firewalls by D. Brent Chapman and Elizabeth D. Zwicky. (See bibliography at the end of this book.)
| Previous | Table of Contents | Next |